The TCP/IP Reference Model and Protocol Suite Explained
TCP/IP means Transmission Control Protocol and Internet Protocol. It is the network model used in the current Internet architecture. TCP/IP that is Transmission Control Protocol and Internet Protocol was developed by Department of Defence’s Project Research Agency (ARPA, later DARPA) as a part of a research project of network interconnection to connect remote machines.
The features that stood out during the research, which led to making the TCP/IP reference model were:
- Support for a flexible architecture. Adding more machines to a network was easy.
- The network was robust, and connections remained intact until the source and destination machines were functioning.
The overall idea was to allow one application on one computer to talk to(send data packets) another application running on different computer.
The TCP/IP protocol suite is a collection of protocols that are used on the Internet. It is usually called TCP/IP after two of its most prominent protocols, but there are other protocols as well.
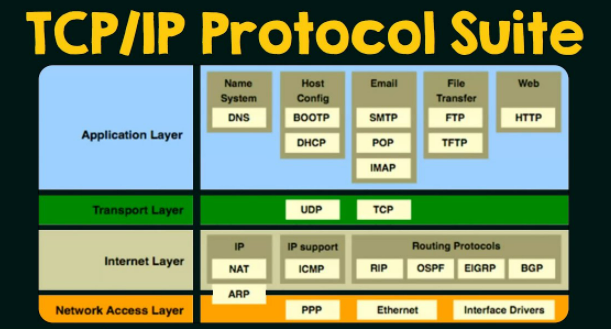
The 4 Layers Layers of TCP/IP Model
Layer 1 : Network Access Layer
The Network Access Layer is the lowest layer of the TCP/IP protocol hierarchy. The protocols in this layer provide the means for the system to deliver data to the other devices on a directly attached network. It defines how to use the network to transmit an IP datagram. Unlike higher-level protocols, Network Access Layer protocols must know the details of the underlying network (its packet structure, addressing, etc.) to correctly format the data being transmitted to comply with the network constraints. The TCP/IP Network Access Layer can encompass the functions of all three lower layers of the OSI reference Model (Network, Data Link, and Physical).
Functions performed at this level include encapsulation of IP datagrams into the frames transmitted by the network, and mapping of IP addresses to the physical addresses used by the network. One of TCP/IP’s strengths is its universal addressing scheme. The IP address must be converted into an address that is appropriate for the physical network over which the datagram is transmitted.
Two examples of RFCs that define network access layer protocols are:
- RFC 826, Address Resolution Protocol (ARP), which maps IP addresses to Ethernet addresses
- RFC 894, A Standard for the Transmission of IP Datagrams over Ethernet Networks, which specifies how IP datagrams are encapsulated for transmission over Ethernet networks
Implementations of the protocols in this layer often appear as a combination of device drivers and related programs. The modules that are identified with network device names usually encapsulate and deliver the data to the network, while separate programs perform related functions such as address mapping.
The Network Access Layer is often ignored by users. The design of TCP/IP hides the function of the lower layers, and the better known protocols (IP, TCP, UDP, etc.) are all higher-level protocols. As new hardware technologies appear, new Network Access protocols must be developed so that TCP/IP networks can use the new hardware. Consequently, there are many access protocols—one for each physical network standard.
The protocols that this layer supports are :
- Ethernet
- Frame Relay
- Token Ring
- ATM
Layer 2 : Internet Layer
The Internet layer defines the protocols which are responsible for logical transmission of data over the entire network. It can be compared to the network layer of the OSI reference model.
The main functions of the internet layer are :
- It transmits data packets to the link layer.
- It routes each of the data packets independently from the source to the destination, using the optimal route.
- It reassembles the out-of-order packets when they reach the destination.
- It handles the error in transmission of data packets and fragmentation of data packets.
The protocols used in this layer are :
- Internet Protocol (IP) − It is a connectionless and unreliable protocol that provides a best effort delivery service. It transports data packets called datagrams that travel over different routes across multiple nodes.
- Address Resolution Protocol (ARP) −This protocol maps the logical address or the Internet address of a host to its physical address, as printed in the network interface card.
- Reverse Address Resolution Protocol (RARP) − This is to find the Internet address of a host when its physical address is known.
- Internet Control Message Protocol (ICMP) − It monitors sending the queries as well as the error messages.
- Internet Group Message Protocol (IGMP) −It allows the transmission of a message to a group of recipients simultaneously.
Layer 3 : Transport Layer
The transport layer is responsible for error-free, end-to-end delivery of data from the source host to the destination host. It corresponds to the transport layer of the OSI reference model.
The functions of the transport layer are :
- It facilitates the communicating hosts to carry on a conversation.
- It provides an interface for the users to the underlying network.
- It can provide for a reliable connection. It can also carry out error checking, flow control, and verification.
The protocols used in this layer are :
- Transmission Control Protocol (TCP) − It is a reliable connection-oriented protocol that transmits data from the source to the destination machine without any error. A connection is established between the peer entities prior to transmission. At the sending host, TCP divides an incoming byte stream into segments and assigns a separate sequence number to each segment. At the receiving host, TCP reorders the segments and sends an acknowledgment to the sender for correct receipt of segments. TCP also manages flow control so that a fast sender does not overwhelm a slow receiver.
- User Datagram Protocol (UDP) − It is a message-oriented protocol that provides a simple unreliable, connectionless, unacknowledged service. It is suitable for applications that do not require TCP’s sequencing, error control or flow control. It is used for transmitting a small amount of data where the speed of delivery is more important than the accuracy of delivery.
- Stream Control Transmission Protocol (SCTP) − It combines the features of both TCP and UDP. It is message oriented like the UDP, which providing the reliable, connection-oriented service like TCP. It is used for telephony over the Internet.
Layer 4 : Application Layer
The application layer is the highest abstraction layer of the TCP/IP model that provides the interfaces and protocols needed by the users. It combines the functionalities of the Session layer, the Presentation layer and the Application layer of the OSI reference model.
The functions of the application layer are :
- It facilitates the user to use the services of the network.
- It is used to develop network-based applications.
- It provides user services like user login, naming network devices, formatting messages, and e-mails, transfer of files etc.
- It is also concerned with error handling and recovery of the message as a whole.
This layer uses a number of protocols, the main among which are as follows :
- Hyper Text Transfer Protocol (HTTP) − It is the underlying protocol for world wide web. It defines how hypermedia messages are formatted and transmitted.
- File Transfer Protocol (FTP) − It is a client-server based protocol for transfer of files between client and server over the network.
- Simple Mail Transfer Protocol (SMTP) − It lays down the rules and semantics for sending and receiving electronic mails (e-mails).
- Domain Name System (DNS) − It is a naming system for devices in networks. It provides services for translating domain names to IP addresses.
- Teletype Network Protocol (TELNET) − It provides bi-directional text-oriented services for remote login to the hosts over the network.
- Simple Network Management Protocol (SNMP) − It is for managing, monitoring the network and for organizing information about the networked devices.



